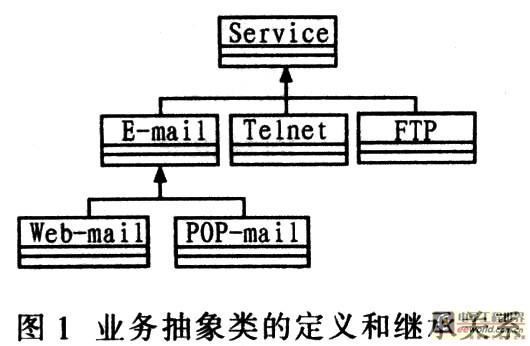
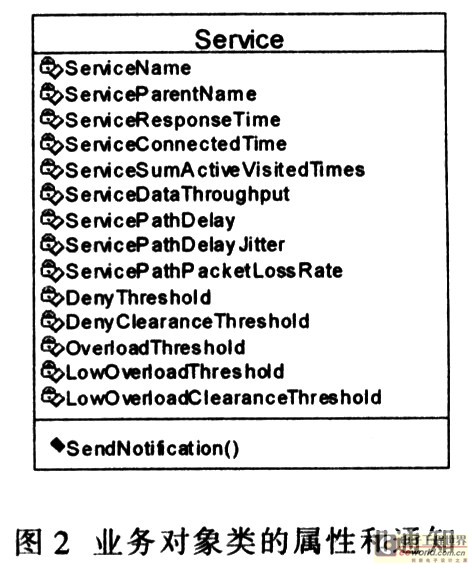
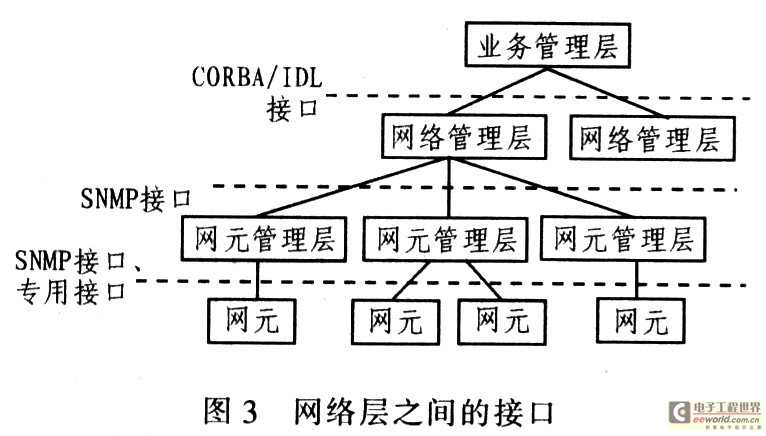
Research and design of the interface between business layer and management layer in business management 1 Introduction The interface between the layers is one of the keys to the design and implementation of the network management system. The interface directly affects the communication efficiency, management functions, and system scalability of the network management system. In the traditional device-oriented network management system, the interface between the network layer and the lower layer is usually a standardized SNMP (Simple Network Man-agement Protocol) interface or CMIP (Common Management Infor-maTIon Protocol) interface or Q3 interface or provided by the developer Dedicated interface. Unlike traditional equipment-oriented network management systems, business-oriented network management takes network business as the managed object, and its management objects and management functions are centered on network business, instead of designing and developing network equipment as the starting point. The device layer cannot and does not need to directly provide a unified information format and a unified interface to the business layer. In the current business-oriented network management system, the system design generally follows a layered design method, that is, from top to bottom are the business layer, network layer and network element layer. Network business management is in the business layer, and it must also be supported by the network layer. The network layer is the basis and support for network business management. The business layer needs to publish corresponding business management tasks to the network layer, by collecting relevant information provided by the network layer, Infer the status of network business, and then carry out network business management. But at present, there is no unified format for the information provided by the network layer upwards, and there is no unified interface specification. Therefore, on the one hand, it is necessary to abstract the ever-changing network services, so as to shield the differences of various upper management services, and at the same time, it is necessary to standardize the information format provided by the network layer to the upper layer, so as to establish a unified and standardized interface between the network layer and the business layer. Drawing on the advanced ideas of active network technology and telecommunications network business management, a service-oriented management model based on active network technology is proposed, and a service-oriented prototype system based on active network technology is developed. In this system, at the network layer and business A unified interface layer is designed and implemented between the layers, so that the network layer and the business layer of the business-oriented network management system can easily communicate, and at the same time improve the scalability of the network management system. 2 Business Abstract Here, computer network applications can be understood as network services, and network services can be understood as network services, and services are defined as end-user-oriented network applications supported by a set of network layer functions. Object-oriented technology has great advantages in describing managed objects, because the object-oriented analysis method is to use object-oriented information modeling concepts (such as entities, relationships, attributes, etc.), while using encapsulation, inheritance, polymorphism and other mechanisms to construct Method of simulating a real system. Therefore, the same method should be used for abstraction when taking network business as a managed object. Using object-oriented technology, a set of relatively complete business abstract principles, abstract methods, abstract granularity, abstract levels, business description methods, etc. are proposed. 2.1 Abstract principles, granularity and level of network business When abstracting network services, the following principles should be followed: (1) The abstracted services should be able to support the complete user functional requirements; (2) Other services provided by the network that are not significant to the business management can not be abstracted as Network management business objects; (3) should follow the principles of unity and consistency, and strive for reusability and compatibility of abstract services. In short, in the business abstraction, it is necessary to fully consider whether the business object is of concern to the user, whether it has management significance for the user, and whether the user can support the complete management function requirements. The granularity of services has a direct impact on the division of management function sub-modules and the mapping with network elements. If the granularity is too large, it is easy to abstract, but it is not conducive to the division of the functional module and the reflection with the network element. If the granularity is too small, it will increase the complexity of the system and the difficulty of implementation. The principle of grasping the granularity is to support the integrity of functions. If a network function cannot complete the complete user functional requirements, it is not defined as a management business object. E.g. The E-mail service needs to verify the user's identity and password. However, for the user, the identity authentication function is not the purpose of using the network, but the security function included in the E-mail service, so it is not defined as an independent service. The abstraction of network services should follow the principles of unity and consistency, so that there is no overlap or ambiguity between abstract network services. Use object-oriented technology to abstract and encapsulate the business, and establish an inheritance relationship between related businesses, so that the defined attributes and management functions can be reused to the greatest extent. For example, E-mail services can be divided into two types, one is Web-based mail, and the other is the mail function realized by POP and SMTP protocols. 2. 2 business abstract examples According to the principles, granularity and level of the above business abstraction, an object-oriented method can be used to abstract the business. From an object-oriented perspective, network services can be regarded as an abstract class, as a common parent class for various concrete network services. Because the characteristics (attributes and services) defined by the network business class can be inherited by each business subclass. For example, services such as FTP, Telnet, and E-mail are all subclasses of the Ser-vice class of network services. The E-mail service is divided into two types, one is Web-based mail, and the other is the mail function using POP and SMTP protocols. Although these two mail services are provided to users in different ways, In the perspective of, they provide the same service, therefore, both their common ground should be extracted to establish mail business objects; and their respective characteristics should be emphasized. Establish corresponding business subclass objects for management, as shown in Figure 1. In a business-oriented network management system, all businesses that can be stored, managed, and operated are marked with a unified abstract name "business object". In fact, business objects are abstractions of managed objects and related supporting resources. According to the idea of ​​object-oriented technology, business objects with the same management operations, attributes, feature groups, notifications and behavior characteristics are combined into a "business object class". "Business object class" is just a virtual concept class, it only describes the category of the class. The business object class can derive a subclass, and the subclass can inherit various characteristics of the parent class, as shown in Figure 2. When a specific business entity exists (creates) as a certain type of business object, the entity is called a business object instance. For the implementation of the interface, when the network layer and the business layer interact, more attributes of the object instance need to be considered. Therefore, the attributes of the object instance need to be described first. The attributes of the object instance mainly include the attribute name, attribute value, and operation characteristics of the attribute. The attribute names in the same class should have unique identification. Attribute values ​​can be read and modified by inherent system means, network activities, or management activities, but modification activities are limited by the operational characteristics of the attributes. When defining business objects, you can specify that certain attributes are read-only to external systems, and you can also specify conditions for changing attribute values. Generally each business object has multiple attributes. To facilitate the management of network services. Define many visible attributes for business objects, such as business name, business type, business response time, business access time, business activity access count, business data throughput, business path delay, business path delay jitter, business path packet loss rate, etc. as shown in picture 2. 3 Design of unified interface The network business management at the business layer needs to be supported by the network layer services. Therefore, the network layer and the business layer interact through interfaces, and the business layer needs to issue corresponding business management tasks to the network layer. By collecting relevant information provided by the network layer. Infer the status of network services, and then manage network services. However, there is no unified format for the information provided by the network layer, and there is no unified interface specification. Because the various devices in the network management system are logically and physically distributed throughout the managed network, and are often in dynamic changes, and CORBA combines object-oriented and distributed processing technology well, its architecture is well solved The problems of object reusability, portability and interoperability are discussed. It is based on the active service PUSH and PULL technology of the event service, which can collect various alarm information and perform information processing in real time; at the same time, the objects can also call each other to provide services, with distributed and transparent support, business objects and components Dynamic migration within the network. To this end, based on the above abstraction of business objects, description of business object attributes and hierarchical structure for business network management, and taking into account the implementation of interfaces, CORBA (Common Object Re-quest Architecture) is introduced. ) Design a unified standardized interface between the business layer and the network layer, as shown in Figure 3. In this standardized interface mode, the communication methods between the various sub-management layers are: (1) The CORBA / IDL interface uses CORBA as the communication platform. The interface information model between the management layers is described by IDL (Interface DefiniTIon Lan-guage, interface definition language), and the C / S interaction mode is used. This interface exists between the business management layer and the network business layer. The communication between the members of each entity uses CORBA / IDL as the communication method between processes. (2) The SNMP interface adopts the SNMP protocol as a method of transmitting information. The interface information model between layers adopts SMI / ASN. 1. Description. Use manager / agent interaction. This interface exists between the network management layer and the network element management layer and between the network element management layer and the network element, and is a standardized interface. (3) Dedicated interface This interface exists only between the network element management layer and the network element, and is generally provided by the manufacturer. 4 Interface description and implementation The interface is implemented by message encapsulation. In the service-oriented network management architecture, in order to manage network services, a protocol data unit PDU (Protocol Data Unit) is defined to describe service data. The fields included in the PDU are serID, serType, serName, serTIme, serAddress, dataLong, and serData. The meaning of each field is as follows serID: indicates the number of the service; serType indicates the type of the service, and different codes indicate the faults, performance, and faults related to the service. 5 functions such as configuration, security, billing, etc .; serName represents the name of the business; serTIme represents the corresponding time for the business management task; serAddress represents the IP address from which the management business task is issued; dataLong represents the total length of the following data in Byte; serData represents the value of each attribute related to the service, including the attribute value described in Figure 3; the business data packet is encapsulated in UDP, followed by the UDP header structure in sequence: 2 bytes of UDP source port number, 2 bytes UDP destination port number, 2 bytes checksum, and 2 bytes message length. The interface defined by CORBA's IDL language is as follows: After converting the IDL model to JAVA source code, generate serviceMes-sageStub. java and serviceMessage Operation. Java and other files. Business data packets are encapsulated in UDP data items. The pile program of the client in the business layer encodes the user's request and sends it to the object realization end. And decode the received processing results, and return the results to the user. The server-side framework program in the network layer decodes the user request, locates the required object method and executes it, encodes the execution result or exception information, and sends it back to the user in the business layer. The client in the business layer requires some specific code to get a reference to the remote object. Once the client code has a reference to the remote object, the method of calling the remote object is the same as using the local method. The code of the network layer server must define the class and instantiate the remote object of the class. After that, the server requires some specific code to register the object and export the method to the client. These exported methods can be called remotely. Both the client code and the server code must access the IDL file defined above to connect the client and the server. 5 Conclusion Discuss in detail the abstract methods of business objects related to interface design and implementation, and describe the properties of business objects in detail. According to the needs of business management, a unified interface layer is designed between the business layer and the network layer, and the description and implementation of the interface are explained. The interface layer is used in a business-oriented network management prototype system based on active network technology. The application results show that the interface layer can facilitate the interaction between the business layer and the network layer and improve the scalability of the network management system. At the same time, because the interface layer shields the differences of the upper layer services, it has transparency to the data format provided by the lower layer, and can be used as a general infrastructure for other business network management systems.
FINGERPRINT BURGLARY SAFES
FINGERPRINT burglary SAFES have passed Chinese 3C certification and are equipped with state of the art fingerprint identification systems.
Details:
These Fingerprint safes have hidden fingerprint verification and high precision scanning;
Our patent: dual system protection is included;
The shelf is removable;
Our safes are side door safes with an independently installed board.
Fingerprint Sensor,Fingerprint Safe Box,Safe Fingerprint,Fingerprint Lock Safe YONGFA INTELLIGENT TECHNOLOGY SECURITY CO., LTD. , http://www.yongfa-safe.com